Imagine that one day the clients of a small firm in the financial sector, whose products operate and are contracted online, cannot access their accounts, make transfers or even access the website. And they encounter the theft of their money, fraudulent use of their cards, movements of money to unknown recipients or misuse of their personal data. Without a doubt, the company would run the risk of incurring very high costs in order to deal with the claims, investigate what happened, repair the damage caused, restore operations, compensate for damages to third parties, regain the trust of its customers, etc.
Secure development helps to make web applications safer to operate and, to a large extent, to ensure the smooth running of a business.
Incidents and the buzz
If there is one event that made fear spread like wildfire among software consumers in 2017, it was the mass hijacking of information perpetrated by the WannaCry virus, which affected banks and businesses around the world. Following this high-profile media event, the IT world would never again be trusted as it used to be.
This incident raised a great deal of interest concerning security, which led the press to increasingly report on the shortcomings of the sector.
A little-known case, but one that clearly shows the importance of secure development, is the one that resulted in a 144-month prison sentence for the two men who stole 160 million credit card numbers using an attack known as SQL Injection. This attack consisted of entering commands in a language understood by databases through user applications. When orders are transferred by an application to databases, the databases execute them and return the requested information normally, due to the fact that the application has the required credentials.
Spanish Small Business, a playground for criminals
The press also reported on the impact on Spanish SMEs, which were the victims of 70% of the attacks in that country, with losses of around 75,000 euros per incident, estimating the total losses at 14 billion euros in one year.
The states have also echoed this circumstance and revealed figures like those from the Attorney General’s Office, which says that in Spain 18,344 proceedings for online fraud (405 convictions), 272 for revealing trade secrets, 295 for computer damage, 68 for crimes against intellectual property and 144 for counterfeiting through ICTs were initiated.
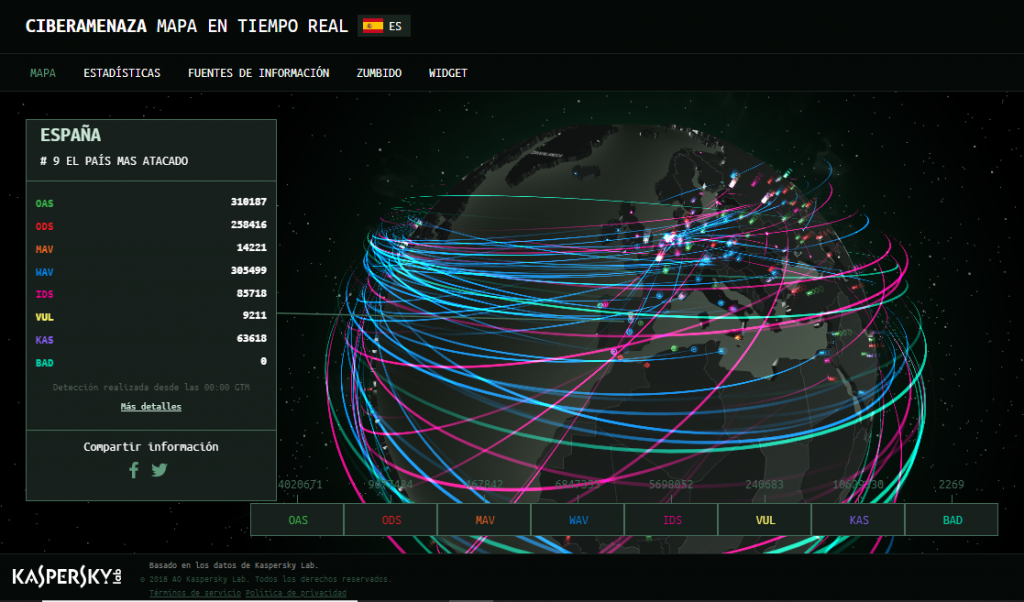
In 2017, 120.000 attacks were detected –a new record for Spain– a rise of 140% in the last two years.
Spain is the ninth most-attacked country, behind Italy in eighth place, and with Russia top of the list. The United States ranks 5th.
The trend: a hybrid combination of social engineering and malware purchasing
Web vulnerabilities base their attack vector on developers being the weak link, so that, by taking advantage of their ignorance, or carelessness, information can be obtained about the application, the system containing it, or users and customers.
But the increasingly sophisticated attacks are not normally based on just one attack vector. They also take into account that a possible incorrect system configuration or user ignorance is a weakness and a way to get information.
Therefore, an uncontrolled error in an application can provide system information to an attacker.
Custom-made applications, the blind spot
There has been a lot of awareness-raising and companies have learnt by investing in protecting their networks against intrusion attempts by using antiviruses, firewalls and advanced system security procedures. But this only slows down one part of the problem.
Attackers have realised that web applications are built with large vulnerabilities that provide a perfect way to collapse the service offered to customers, corrupt or steal data, or obtain information about other vulnerabilities in the server-client infrastructure.
We could compare this fact graphically to equipping a house with a security door and leaving the keys under the doormat.
“More than 70% of security vulnerabilities exist in the application layer, posing a significant and immediate threat to users worldwide”, said the recently deceased Howard A. Schmidt, CISSP, board member of (ISC)² and chairman of the Information Security Forum (ISF). “Too often, security is established at the end of the software life-cycle in response to a threat or risk.”
It is estimated that 86% of websites have at least one vulnerability, and the probability of information leakage is 56%.
Identifying the risk, the black book of applications
“There are two types of companies: those that have been hacked and those that are still not aware that they have been hacked” John Chambers, former CEO, Cisco
The IMF, which is concerned about the subject, has produced a very revealing report on cyber risks in the financial sector, including mathematical calculation models.
The report focuses on the most vulnerable players in the sector (Fintech), the threats and risk measurement.
Of the risks considered to be major risks to the economy, the report highlights cyber risk as the greatest of all, even greater than geopolitical risk; and the US financial sector as the sector that most reports on the attacks that it suffers. This reveals the concern of American financial institutions for creating a joint security environment.
This is not the case in other countries, where there is no incentive to report incidents at the private level. Nor is there much information in the public environment, perhaps due to the restrictions deemed necessary for national security.
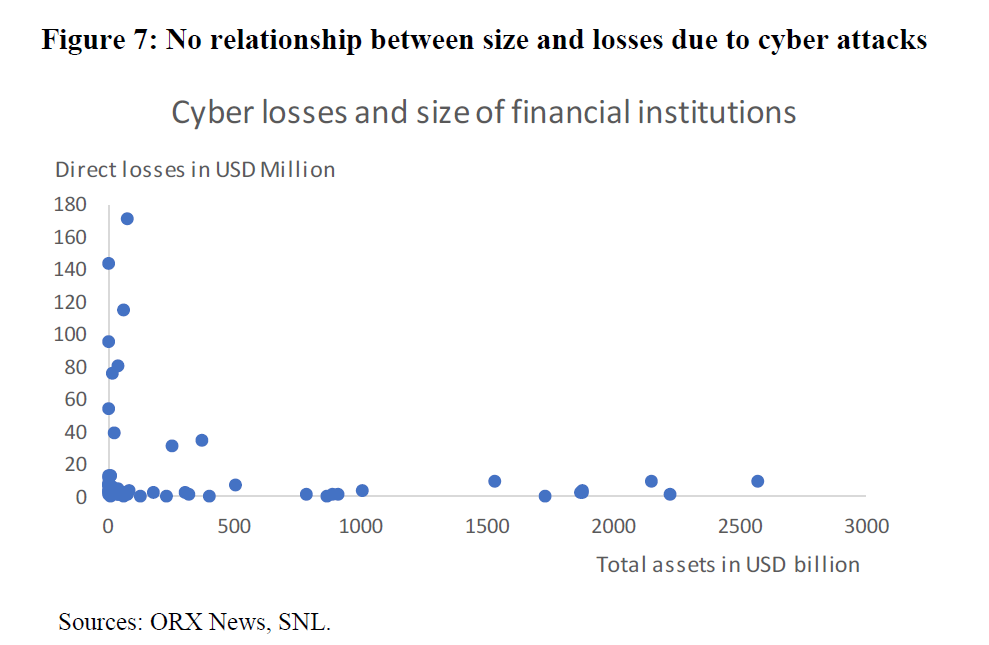
In regard to this market, the report emphasises the great difference between the impact of the attacks and the size of the victim: the smaller the company, the greater the impact of the attacks.
According to the report, this is not because the attackers have a preference for Fintechs, but because Fintechs are not able to allocate as many resources to cyber-security as the major banks.
The main threats you may encounter include: business disruption (very important if you are an online store or have many concurrent operations), fraud, information leaks (especially if you handle very sensitive information, such as medical records), and reputational risk.
You can get a better picture of the risk you run if you consider which of the above threats your business faces, what the weak links or vulnerabilities may be (in applications, the system or the users), and what consequences a threat could have if it became a reality through a successful attack.
Calculation of risk:
Risk = f (Threat, Vulnerability, Impact/Consequences)
The financial sector has a high level of threat, as it is targeted by criminals, activists and spies.
In addition, technological proliferation puts Fintechs at a very high level of vulnerability. The number of exposed applications and how they are constructed are of great importance in this area.
Value-added solutions, turning costs into profits
Although zero risk does not exist, there is a lot you can do to mitigate the risks in your custom applications.
If you are a software supplier, you can make the production of your application more secure by implementing a Development Security Maturity Model. This consists of a series of good practices to be integrated right from the beginning of the Development Life Cycle. Knowledge of these good practices and their implementation will allow you to raise the levels of maturity, and therefore create safer applications.
There is a great project-based open framework (www.owasp.org), with applications, testing guides, methodologies and enough information to implement good security practices in the development life cycle of your projects.
It is important that, when training users, reliable sources should be quoted and any other sources questioned.
If you are a small company, you can ask your supplier to inform you about the good practices that will be used in the development of the software that you are going to contract, whether they have a security maturity model during development, or if they use the services of an external company to provide web auditing services, web intrusion testing, training in secure development, or support for the resolution of vulnerabilities.
If your software provider is not mature enough, or you consider that you need to take extra steps, as the customer, you can contract the services of an external company to manage all the security requirements.
Whichever option you choose, it is important to implement it right from the beginning of the project, in order to reduce costs.
As a software consumer company, you will need to have detailed information on reliable sources that supply the application you are purchasing: what data will be requested at any given time (especially passwords), what information will arrive by email, and which representatives are reliable in the event of incidents or doubts.
Whether your company is a consumer or a builder, you must bear in mind that security incidents will appear throughout development, and even once the product has been implemented. You must therefore take into account the possible time-frames for resolution, even before they appear.
You must consider, for maintenance too, the good practices of safe development and the methods for resolving the vulnerabilities that will appear throughout the lifetime of the product.
Finally, insurance is available to cover cyber risks, with products suitable for SMEs and the self-employed. Whether you are a supplier or a consumer, it is a good idea to consult your insurance agent and seek products that fit your cyber risks.


