In March 2018, an investigation by The Guardian and The New York Times revealed one of the most serious technological scandals of the decade: consultancy firm Cambridge Analytica had illegally obtained the personal data of up to 87 million users through Facebook. The data leak originated from an application called “This is your digital life”, a seemingly harmless online personality test which the consultancy firm used to search for and establish socio-political profiles thanks to Big Data, therefore predicting and influencing election results.
This scandal, which culminated in the closure of Cambridge Analytica and the appearance of Mark Zuckerberg before the European Parliament, thrust the importance of data protection into the spotlight in the age of Big Data and social networks. Although it was one of the most high-profile cases, it was not the first confidential data leak, nor the largest in recent times.
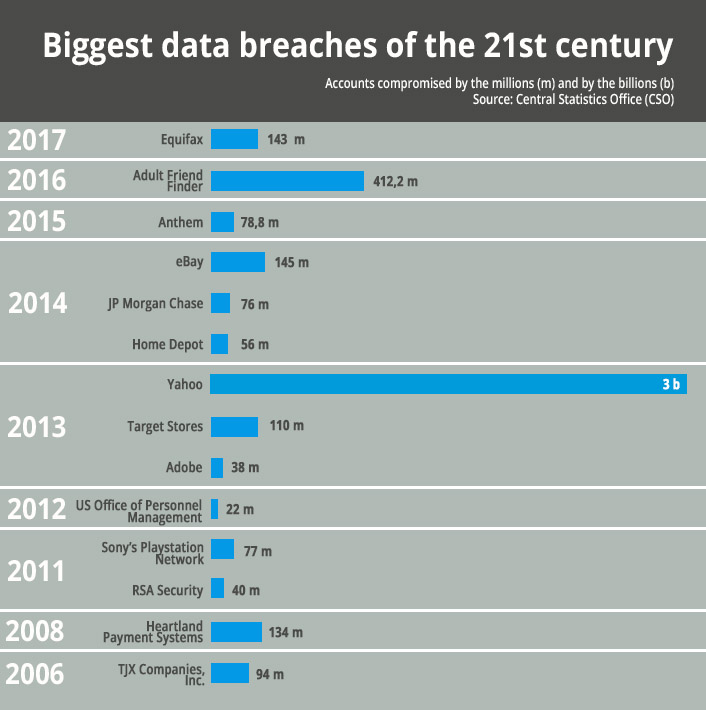
As the graphic reveals, the largest leak in the last decade came from Yahoo, and in the majority of cases users are not aware that they have been affected because few companies inform their users when this occurs. How can we find out if we have been hacked? We have various online tools that enable us to check if we have been affected.
Tools against data leaks
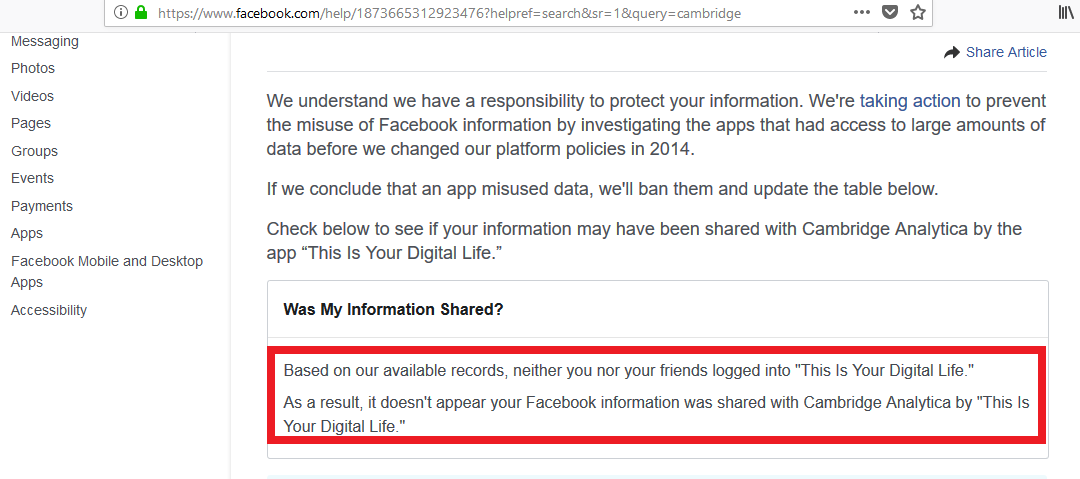
Facebook has been informing its clients affected by the Cambridge Analytica leak, but if we want to be completely sure that our data has not been revealed we need to verify that from our own profile on the Facebook help page. In this test, the red box reveals that neither the user nor their friends logged in to the “This is your digital life” application, and therefore, no data was shared with Cambridge Analytica.
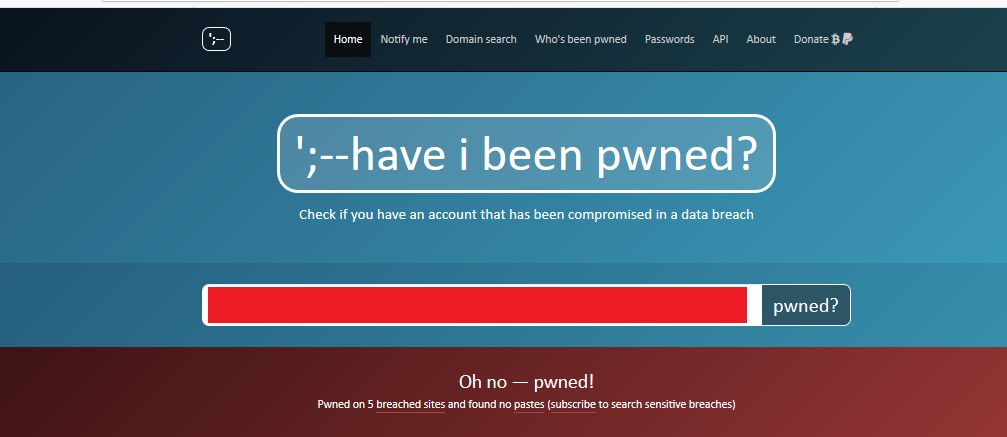
The website Have I Been Pwned?, created by Microsoft cybersecurity specialist Troy Hunt, shows if your email has been exposed to cybersecurity violations. The website has registered around 4 million affected accounts and is very popular among information security specialists. In this case, the email address we entered has been affected. As we can see, the tool even tells us when and through what platform the leak occurred.
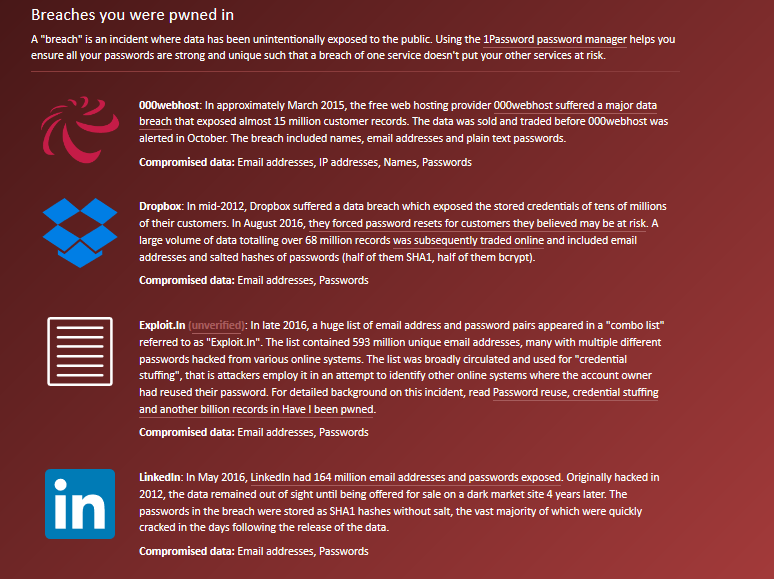
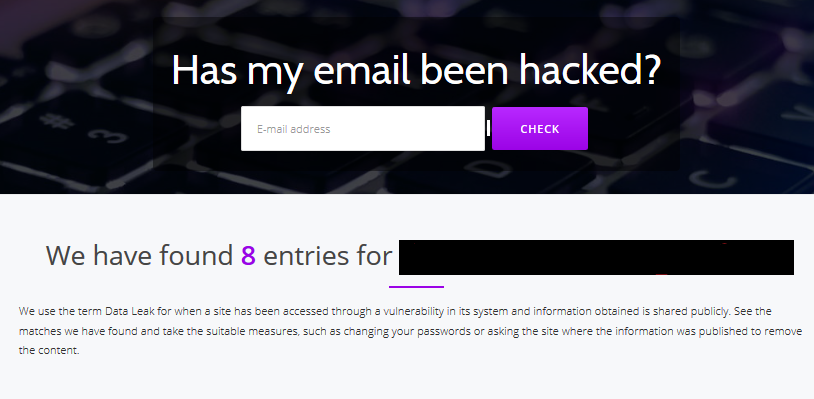
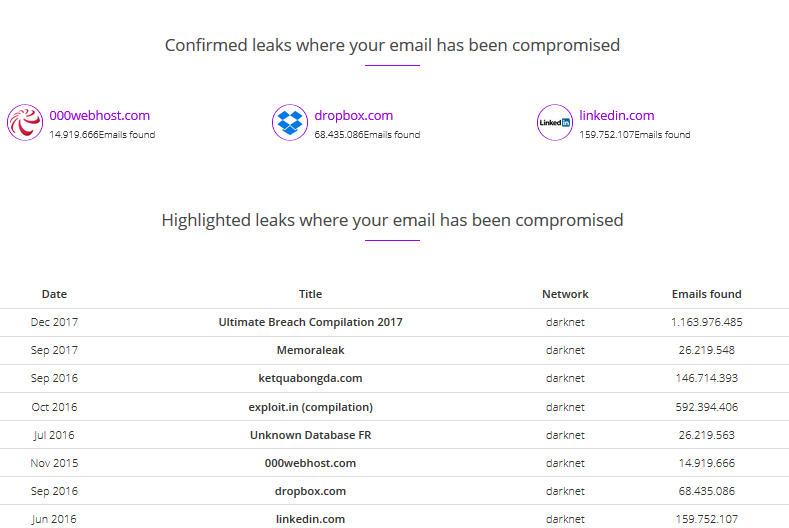
The website Hacked-Emails has additional databases to the website developed by Troy Hunt. Verifying your email address in the database is also highly recommended because it has a DNS in Spanish: hesidohackeado.com. As we can see in the image, after verifying the same account used previously, the website shows us other sites where our data has been leaked.
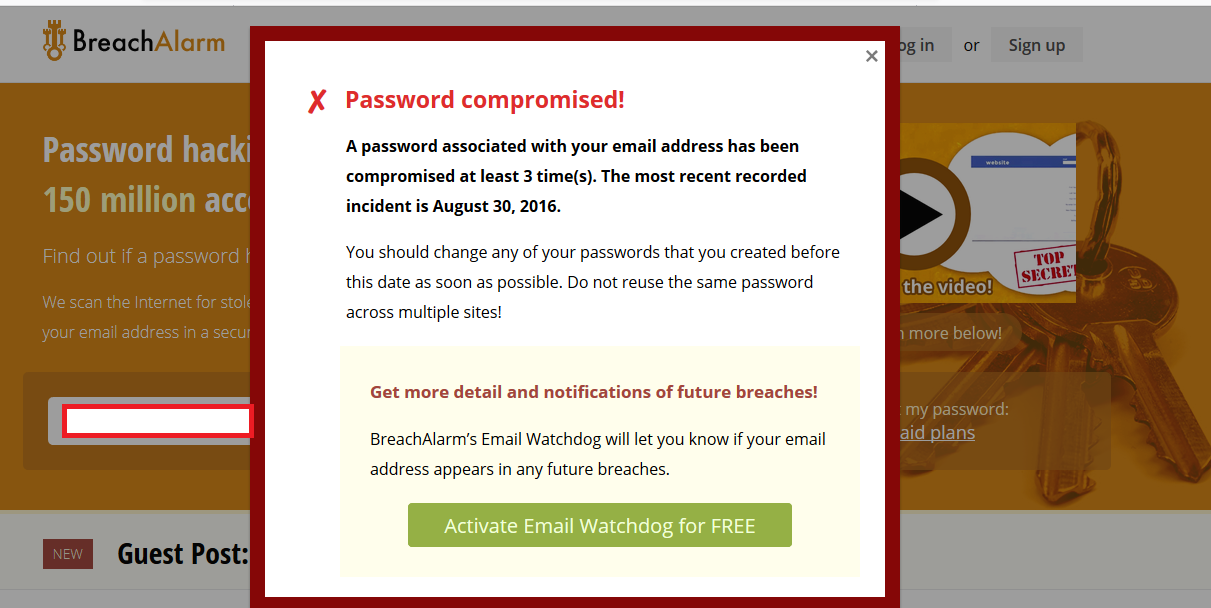
In addition to informing of cases of hacking that have already occurred, Breach Alarm offers something new: the possibility to receive an alert in real time if your email is involved in any type of attack.
What to do in the event of hacking?
We have just seen that we have been hacked. What should we do if our data has been compromised. How big could the leak be?
• Change your passwords on the websites where you have been affected. The longer and more complex the password, the more secure it is. If you cannot think of one, you can use a secure password generator such as pwgen, which has versions for Windows and Linux. We do not recommend online generators, because they could store generated passwords and use them in the event of a cybersecurity attack.
• Do not re-use passwords, especially if you have been affected by a leak, because these will have been published on the “Dark web”, a part of the internet that will not appear on search engines and that is often used for criminal activities. If they are difficult to remember, use a Password Manager to store your passwords securely. It works like an agenda for all your passwords, which can only be opened with a master password. This remains the method most recommended by specialists to avoid repeating passwords on different websites or using weak passwords, but if the hackers get hold of the master password they will have access to the other ones too.
• Be careful with the security questions. If you use them, make sure only you know the answers to them.
• Add a 2nd Factor Authentication (2FA) to your email account if possible to strengthen your credentials. The main email services (Gmail, Hotmail y Yahoo) allow this.
• Delete the affected email account to avoid future leaks from the same account.
• Do not accept third-party applications on social networks that have access to your data. To review the permissions for these applications on Facebook, go to the page “Applications and websites” once you have logged in.
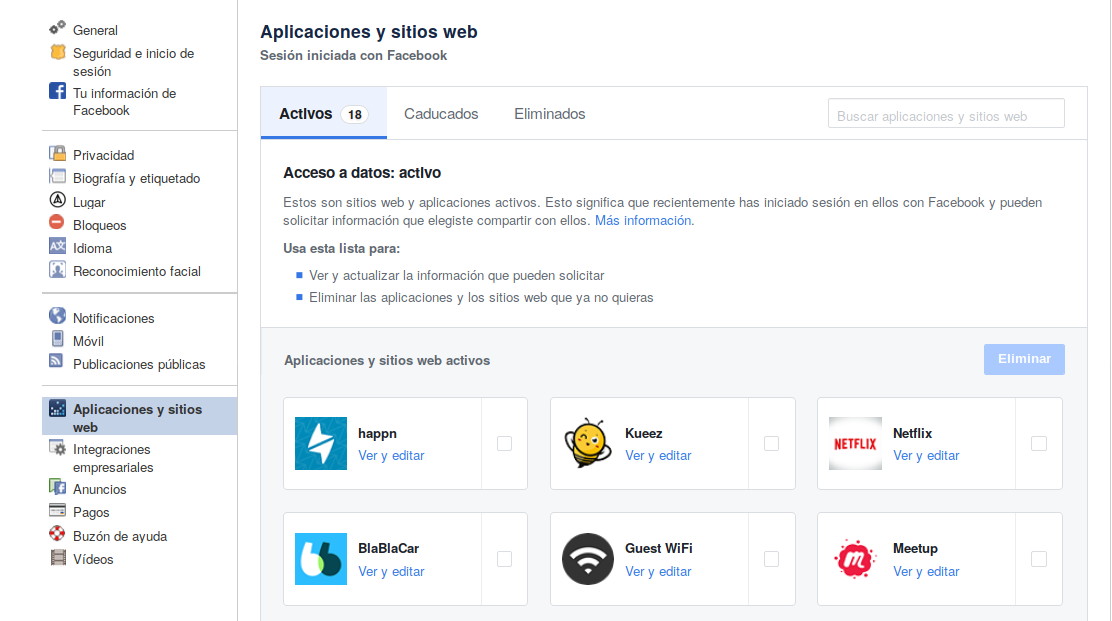
Bear in mind that data transferred to third parties not only includes your list of friends and personal data, but also photographs and “likes” which can reveal sensitive data such as your political leanings, beliefs, etc.
In conclusion, in the age of Big Data, both the data we reveal and the way third parties use this data is important. By entering our data under the philosophy “I have nothing to hide,” we are conceding our right to privacy without knowledge of the true scope of this concession. In the cases of Cambridge Analytica and the surveillance program revealed by Edward Snowden, the consequences are sometimes not clear, and do not solely affect the person whose data was disclosed.
The users who authorised “This is you digital life” did not imagine that a personality test could use their sexual orientation or union affiliations to influence electoral results, neither were they aware that they were effectively selling access to the profiles of friends and families. When a product or service is free, we are the product (or the equivalent to us, our data).


